Network Egress Firewall
Introduction
Security is important to every customer. The principle of least privilege is a common security practice that limits an application’s access to only those resources it needs to operate. For example, if we know an application does not need access to the Internet, we should create a policy to block that application’s access to the Internet.
In the real world, customers will solve this challenge with outbound proxies/VLANs/firewalls, but those solutions can be expensive and complex to implement. Now we will show OpenShift Virtualization allows us to add an additional layer of security with just a few button clicks.
In this module, you will test blocking egress access from a Windows virtual machine to the Internet with the built-in, cloud native features of OpenShift.
Access the Internet from a Windows virtual machine
-
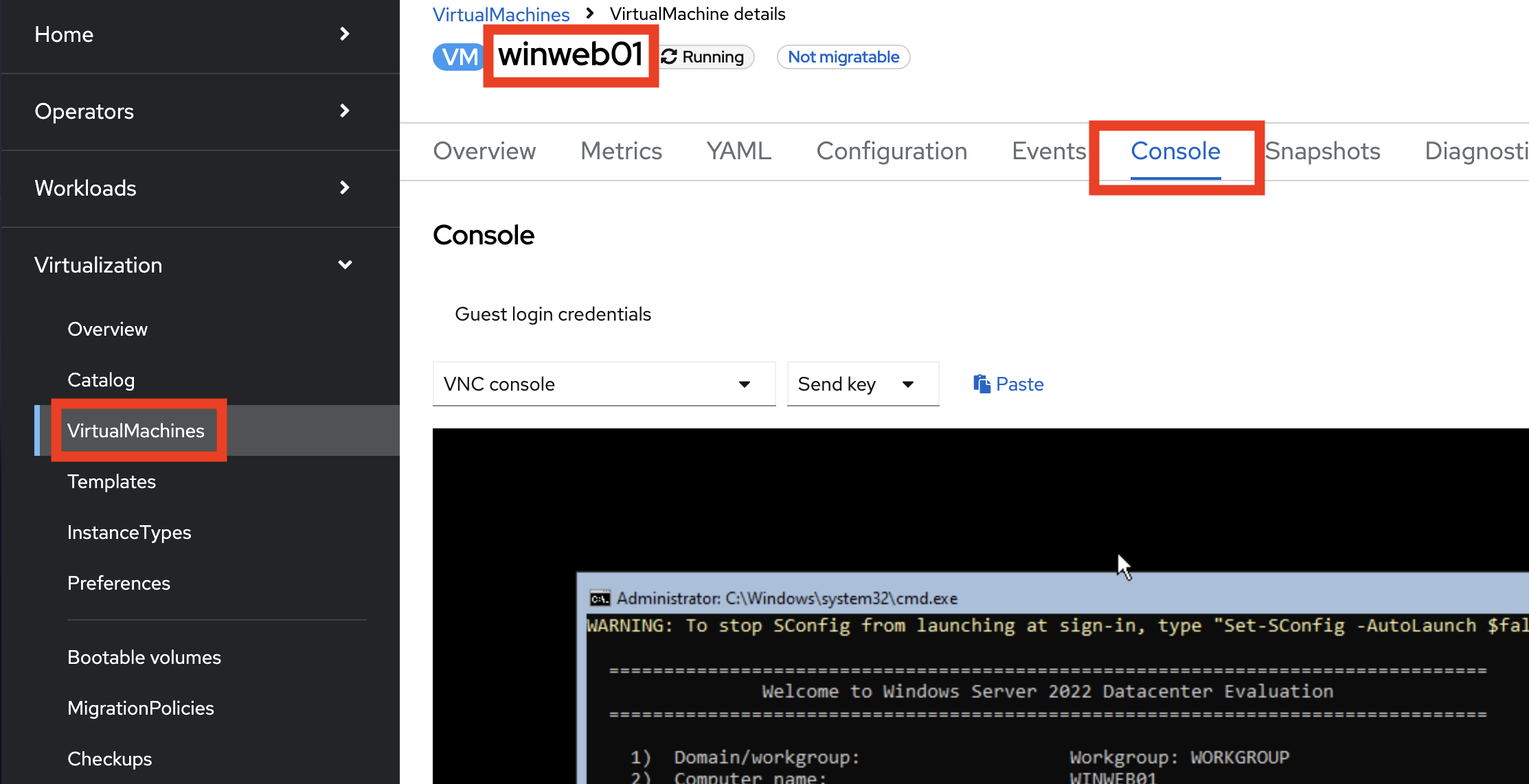
Click VirtualMachines, click winweb01 then click the Console tab. You are already logged into the windows virtual machine’s administrative interface.
-
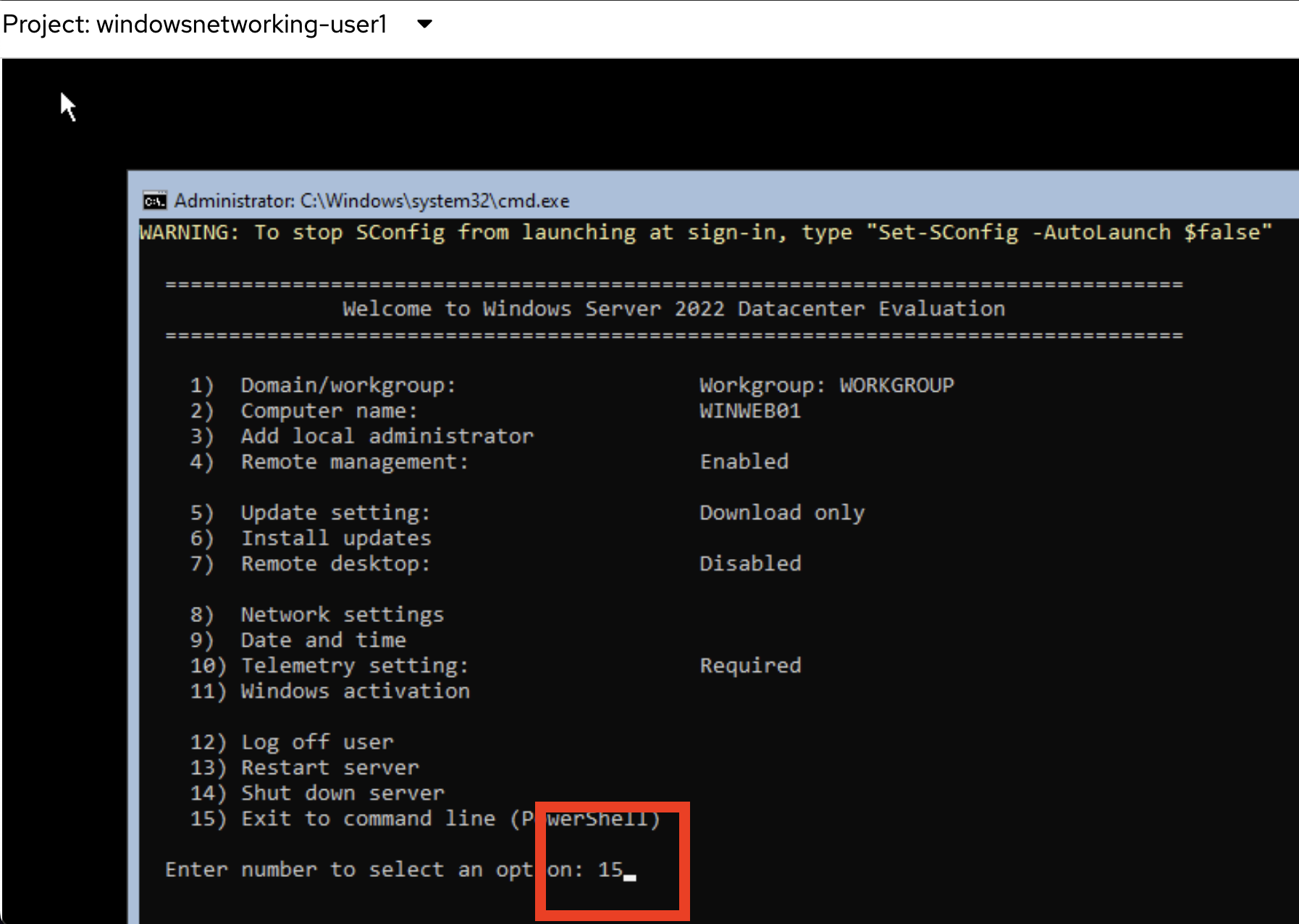
Type
15and hit Enter to start Powershell -
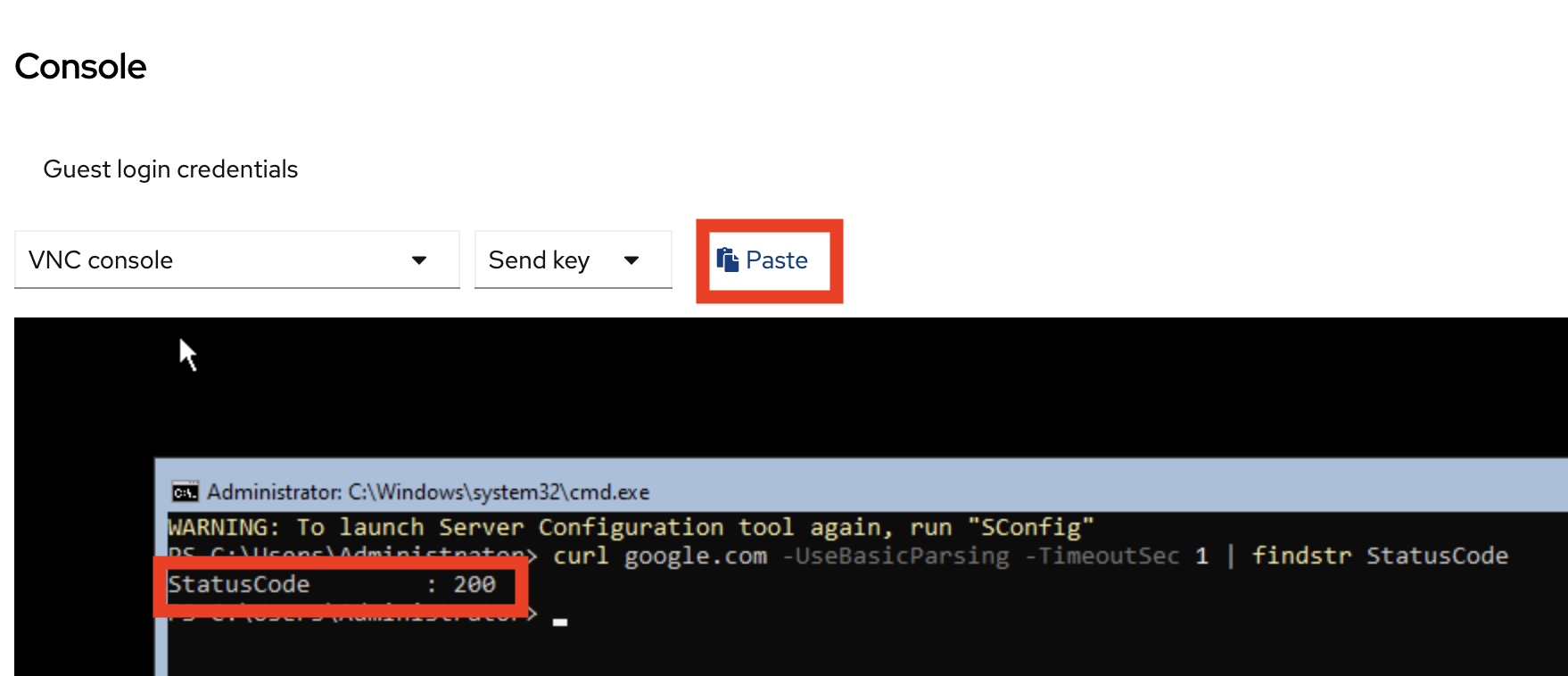
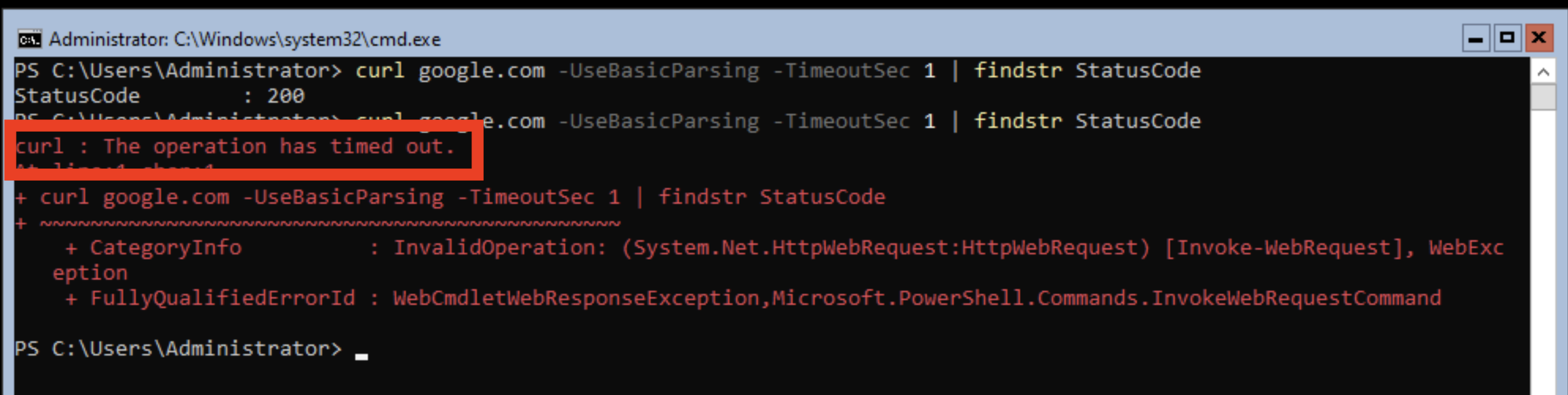
Copy the following command and paste it into the virtual machine console with the special paste button. Click into the virtual machine console and hit Enter. Notice that the connection succeeds with
StatusCode: 200curl google.com -UseBasicParsing -TimeoutSec 1 | findstr StatusCode
Implement a Network Policy to Block Egress
-
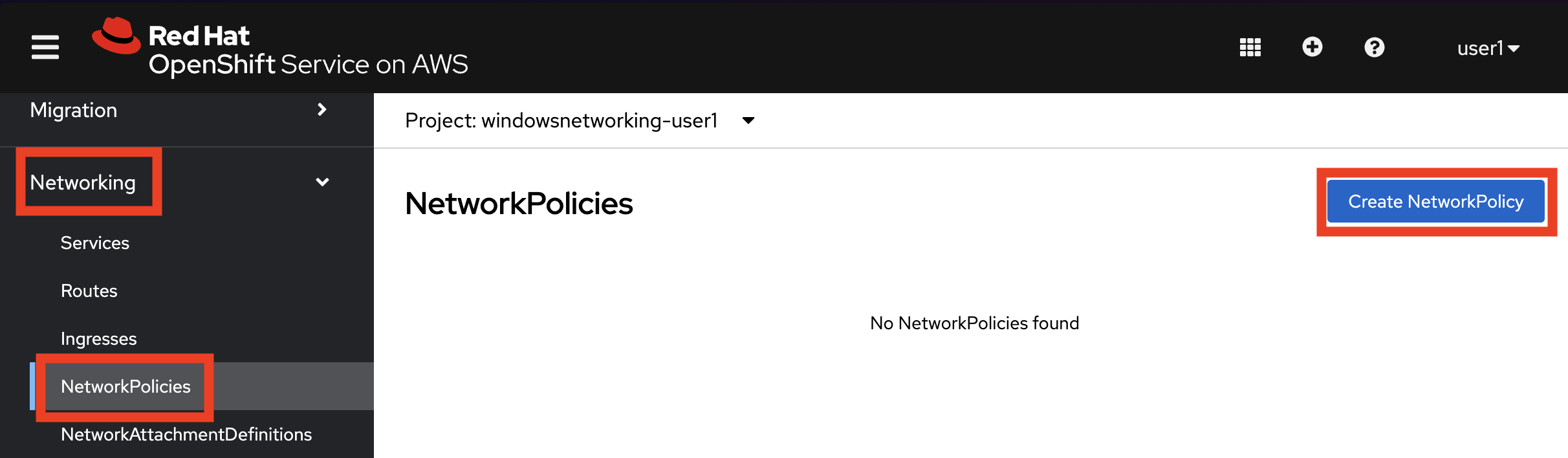
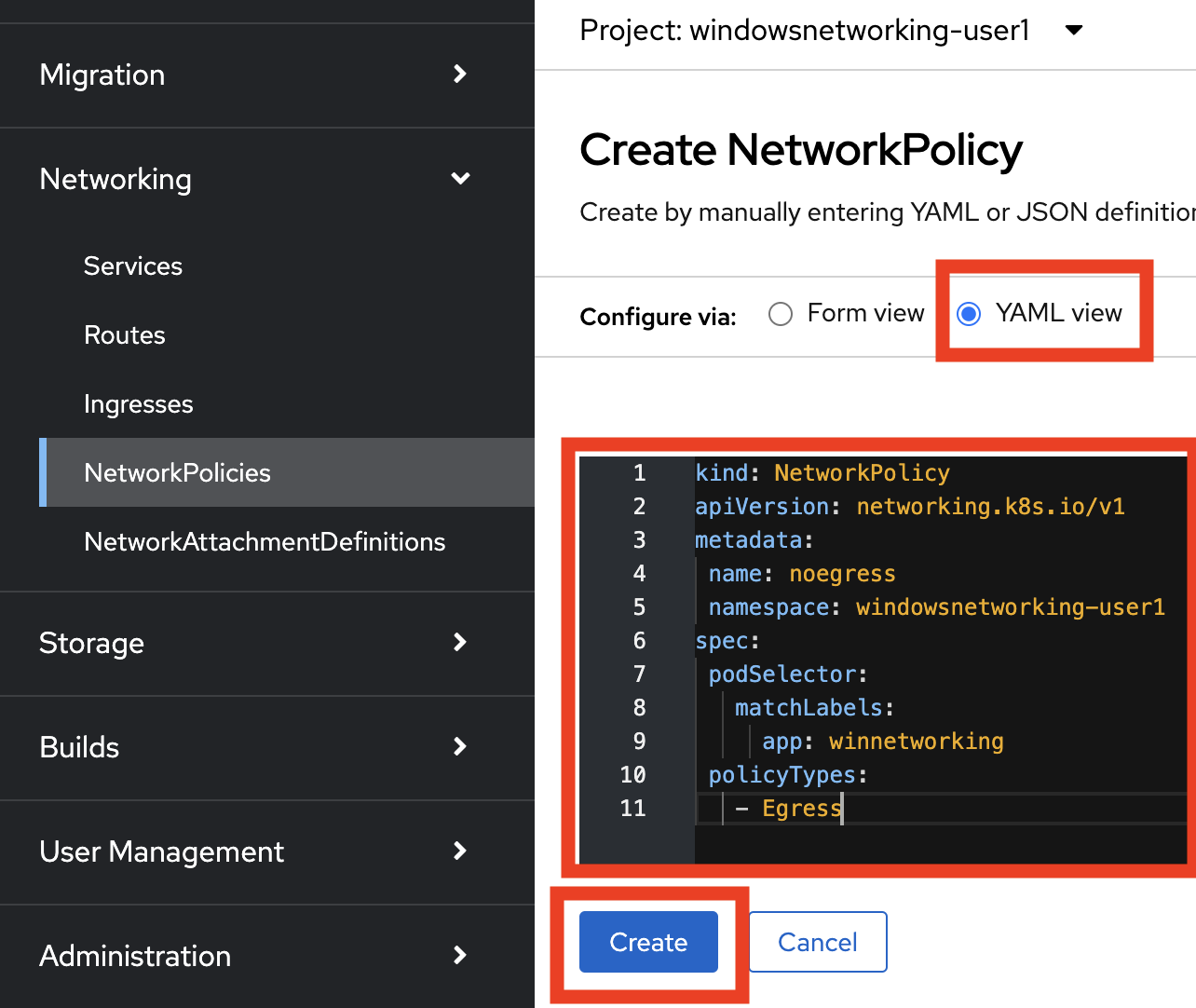
On the left side, click Networking → NetworkPolicies → Create NetworkPolicy.
-
Select the YAML View radio button.
-
Replace the sample YAML with the following NetworkPolicy, make sure to use the correct namespace.
kind: NetworkPolicy apiVersion: networking.k8s.io/v1 metadata: name: noegress namespace: windowsmesh-userX spec: podSelector: matchLabels: app: winmesh policyTypes: - Egress -
Click Create when your console looks as follows.
Validate that Internet Access is Blocked from the Windows virtual machine
-
Go back to the Powershell and test the network connection to the Internet. Click Virtualization → VirtualMachines → winweb01 → Console Click into the console and repeat the Internet access test. To run the same command again, press the Up Arrow and hit Enter
The egress to Internet connection has been denied with a timeout.